CCNA 1 Introduction to Networks Ver 6.0 – ITN Chapter 5 Exam Answers
CCNA 1 Chapter 5 Exam Answers
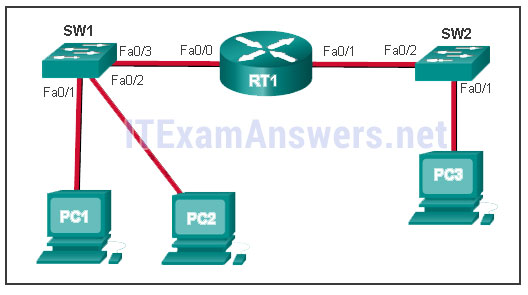
- Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
- PC2 will send an ARP reply with its MAC address.
- RT1 will send an ARP reply with its Fa0/0 MAC address.
- RT1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with its Fa0/1 MAC address.
- What statement describes Ethernet?
- It defines the most common LAN type in the world.
- It is the required Layer 1 and 2 standard for Internet communication.
- It defines a standard model used to describe how networking works.
- It connects multiple sites such as routers located in different countries.
- Which two statements describe features or functions of the logical link control sublayer in Ethernet standards? (Choose two.)
- Logical link control is implemented in software.
- Logical link control is specified in the IEEE 802.3 standard.
- The LLC sublayer adds a header and a trailer to the data.
- The data link layer uses LLC to communicate with the upper layers of the protocol suite.
- The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
- What statement describes a characteristic of MAC addresses?
- They must be globally unique.
- They are only routable within the private network.
- They are added as part of a Layer 3 PDU.
- They have a 32-bit binary value.
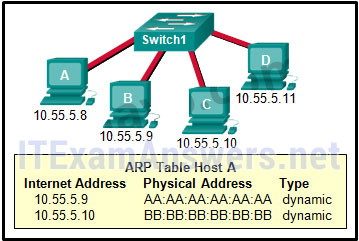
- Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
- Host A sends an ARP request to the MAC address of host D.
- Host D sends an ARP request to host A.
- Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds.
- Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
- Which statement is true about MAC addresses?
- MAC addresses are implemented by software.
- A NIC only needs a MAC address if connected to a WAN.
- The first three bytes are used by the vendor assigned OUI.
- The ISO is responsible for MAC addresses regulations.
- Which destination address is used in an ARP request frame?
- 0.0.0.0
- 255.255.255.255
- FFFF.FFFF.FFFF
- 127.0.0.1
- 01-00-5E-00-AA-23
- What addressing information is recorded by a switch to build its MAC address table?
- the destination Layer 3 address of incoming packets
- the destination Layer 2 address of outgoing frames
- the source Layer 3 address of outgoing packets
- the source Layer 2 address of incoming frames
- Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?
- The switch will discard the frame.
- The switch will forward the frame only to port 2.
- The switch will forward the frame to all ports except port 4.
- The switch will forward the frame to all ports.
- The switch will forward the frame only to ports 1 and 3.
- Which switching method uses the CRC value in a frame?
- cut-through
- fast-forward
- fragment-free
- store-and-forward
- What is auto-MDIX?
- a type of Cisco switch
- an Ethernet connector type
- a type of port on a Cisco switch
- a feature that detects Ethernet cable type
- What happens to runt frames received by a Cisco Ethernet switch?
- The frame is dropped.
- The frame is returned to the originating network device.
- The frame is broadcast to all other devices on the same network.
- The frame is sent to the default gateway.
- What are the two sizes (minimum and maximum) of an Ethernet frame? (Choose two.)
- 56 bytes
- 64 bytes
- 128 bytes
- 1024 bytes
- 1518 bytes
- True or False?
When a device is sending data to another device on a remote network, the Ethernet frame is sent to the MAC address of the default gateway.- true
- false
- The ARP table in a switch maps which two types of address together?
- Layer 3 address to a Layer 2 address
- Layer 3 address to a Layer 4 address
- Layer 4 address to a Layer 2 address
- Layer 2 address to a Layer 4 address
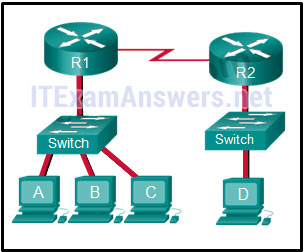
- Refer to the exhibit. The switches are in their default configuration. Host A needs to communicate with host D, but host A does not have the MAC address for its default gateway. Which network hosts will receive the ARP request sent by host A?
- only host D
- only router R1
- only hosts A, B, and C
- only hosts A, B, C, and D
- only hosts B and C
- only hosts B, C, and router R1
- Which statement describes the treatment of ARP requests on the local link?
- They must be forwarded by all routers on the local network.
- They are received and processed by every device on the local network.
- They are dropped by all switches on the local network.
- They are received and processed only by the target device.
- What are two potential network problems that can result from ARP operation? (Choose two.)
- Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
- On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays.
- Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.
- Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
- Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
- Fill in the blank.
A collision fragment, also known as a RUNT frame, is a frame of fewer than 64 bytes in length. - Fill in the blank.
On a Cisco switch, port-based memory buffering is used to buffer frames in queues linked to specific incoming and outgoing ports. - Fill in the blank.
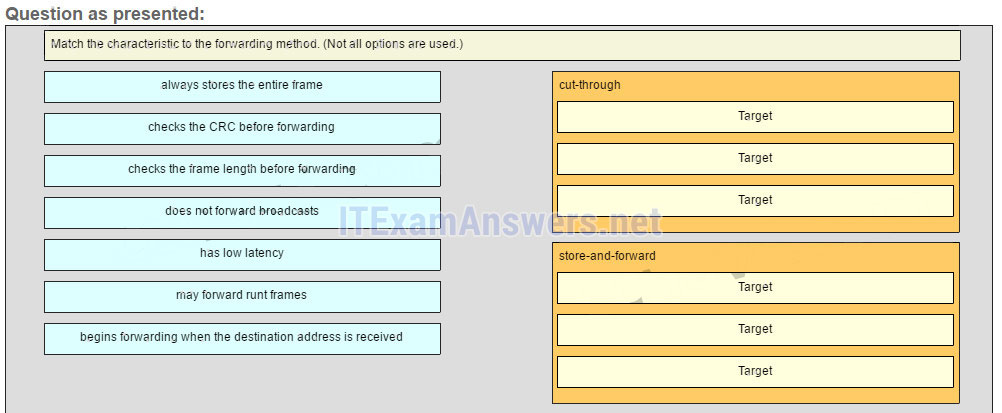
ARP spoofing is a technique that is used to send fake ARP messages to other hosts in the LAN. The aim is to associate IP addresses to the wrong MAC addresses. - Match the characteristic to the forwarding method. (Not all options are used.)
Last Updated on May 20, 2021 by
Cisco CCNA 1 ITN v6.0 chapter 5 Exam Answers Routing and Switching (R&S) Introduction to Networks (ITN) (Version 6.00) collection year 2017, 2018 and 2019 Full 100%. CCNA 1 has been know as ITN. The following are the questions exam answers. Guarantee Passed 100%. CCNA 1 v6.0 chapter 5 exam answers has some new update from the old version 5.1. You can review all chapter 5 Exam Answers. You will get passed scored 100% with this version 6.0. Good Luck for Cisco Netacad ITN v6.0 Exam!
-
Recommend
Noted: There are 3 questions(23, 24, 25) were updated in March, 2019.
-
What happens to runt frames received by a Cisco Ethernet switch?
- The frame is dropped.
- The frame is returned to the originating network device.
- The frame is broadcast to all other devices on the same network.
- The frame is sent to the default gateway.
Explanation:
In an attempt to conserve bandwidth and not forward useless frames, Ethernet devices drop frames that are considered to be runt (less than 64 bytes) or jumbo (greater than 1500 bytes) frames.
-
What are the two sizes (minimum and maximum) of an Ethernet frame? (Choose two.)
- 56 bytes
- 64 bytes
- 128 bytes
- 1024 bytes
- 1518 bytes
Explanation:
The minimum Ethernet frame is 64 bytes. The maximum Ethernet frame is 1518 bytes. A network technician must know the minimum and maximum frame size in order to recognize runt and jumbo frames.
-
What statement describes Ethernet?
- It defines the most common LAN type in the world.
- It is the required Layer 1 and 2 standard for Internet communication.
- It defines a standard model used to describe how networking works.
- It connects multiple sites such as routers located in different countries.
Explanation:
Ethernet is the most common LAN protocol in the world. It operates at Layer 1 and 2, but is not required for Internet communication. The OSI model is used to describe how networks operate. A WAN connects multiple sites located in different countries.
-
Which two statements describe features or functions of the logical link control sublayer in Ethernet standards? (Choose two.)
- Logical link control is implemented in software.
- Logical link control is specified in the IEEE 802.3 standard.
- The LLC sublayer adds a header and a trailer to the data.
- The data link layer uses LLC to communicate with the upper layers of the protocol suite.
- The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
Explanation:
Logical link control is implemented in software and enables the data link layer to communicate with the upper layers of the protocol suite. Logical link control is specified in the IEEE 802.2 standard. IEEE 802.3 is a suite of standards that define the different Ethernet types. The MAC (Media Access Control) sublayer is responsible for the placement and retrieval of frames on and off the media. The MAC sublayer is also responsible for adding a header and a trailer to the network layer protocol data unit (PDU).
-
What statement describes a characteristic of MAC addresses?
- They must be globally unique.
- They are only routable within the private network.
- They are added as part of a Layer 3 PDU.
- They have a 32-bit binary value.
Explanation:
Any vendor selling Ethernet devices must register with the IEEE to ensure the vendor is assigned a unique 24-bit code, which becomes the first 24 bits of the MAC address. The last 24 bits of the MAC address are generated per hardware device. This helps to ensure globally unique addresses for each Ethernet device.
-
Which statement is true about MAC addresses?
- MAC addresses are implemented by software.
- A NIC only needs a MAC address if connected to a WAN.
- The first three bytes are used by the vendor assigned OUI.
- The ISO is responsible for MAC addresses regulations.
Explanation:
A MAC address is composed of 6 bytes. The first 3 bytes are used for vendor identification and the last 3 bytes must be assigned a unique value within the same OUI. MAC addresses are implemented in hardware. A NIC needs a MAC address to communicate over the LAN. The IEEE regulates the MAC addresses.
-
Which destination address is used in an ARP request frame?
- 0.0.0.0
- 255.255.255.255
- FFFF.FFFF.FFFF
- 127.0.0.1
- 01-00-5E-00-AA-23
Explanation:
The purpose of an ARP request is to find the MAC address of the destination host on an Ethernet LAN. The ARP process sends a Layer 2 broadcast to all devices on the Ethernet LAN. The frame contains the IP address of the destination and the broadcast MAC address, FFFF.FFFF.FFFF.
-
What addressing information is recorded by a switch to build its MAC address table?
- the destination Layer 3 address of incoming packets
- the destination Layer 2 address of outgoing frames
- the source Layer 3 address of outgoing packets
- the source Layer 2 address of incoming frames
Explanation:
A switch builds a MAC address table by inspecting incoming Layer 2 frames and recording the source MAC address found in the frame header. The discovered and recorded MAC address is then associated with the port used to receive the frame.
-
Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?
Cisco ITN CCNA 1 v6.0 Chapter 5 Exam Answer R&S 2018 2019 001 - The switch will discard the frame.
- The switch will forward the frame only to port 2.
- The switch will forward the frame to all ports except port 4.
- The switch will forward the frame to all ports.
- The switch will forward the frame only to ports 1 and 3.
Explanation:
The MAC address of PC3 is not present in the MAC table of the switch. Because the switch does not know where to send the frame that is addressed to PC3, it will forward the frame to all the switch ports, except for port 4, which is the incoming port.
-
Which switching method uses the CRC value in a frame?
- cut-through
- fast-forward
- fragment-free
- store-and-forward
Explanation:
When the store-and-forward switching method is used, the switch receives the complete frame before forwarding it on to the destination. The cyclic redundancy check (CRC) part of the trailer is used to determine if the frame has been modified during transit. In contrast, a cut-through switch forwards the frame once the destination Layer 2 address is read. Two types of cut-through switching methods are fast-forward and fragment-free.
-
What is auto-MDIX?
- a type of Cisco switch
- an Ethernet connector type
- a type of port on a Cisco switch
- a feature that detects Ethernet cable type
Explanation:
Auto-MDIX is a feature that is enabled on the latest Cisco switches and that allows the switch to detect and use whatever type of cable is attached to a specific port.
-
True or False?
When a device is sending data to another device on a remote network, the Ethernet frame is sent to the MAC address of the default gateway.
- true
- false
Explanation:
A MAC address is only useful on the local Ethernet network. When data is destined for a remote network of any type, the data is sent to the default gateway device, the Layer 3 device that routes for the local network.
-
The ARP table in a switch maps which two types of address together?
- Layer 3 address to a Layer 2 address
- Layer 3 address to a Layer 4 address
- Layer 4 address to a Layer 2 address
- Layer 2 address to a Layer 4 address
Explanation:
The switch ARP table keeps a mapping of Layer 2 MAC addresses to Layer 3 IP addresses. These mappings can be learned by the switch dynamically through ARP or statically through manual configuration.
-
Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
Cisco ITN CCNA 1 v6.0 Chapter 5 Exam Answer R&S 2018 2019 002 - PC2 will send an ARP reply with its MAC address.
- RT1 will send an ARP reply with its Fa0/0 MAC address.
- RT1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with its Fa0/1 MAC address.
Explanation:
When a network device wants to communicate with another device on the same network, it sends a broadcast ARP request. In this case, the request will contain the IP address of PC2. The destination device (PC2) sends an ARP reply with its MAC address.
-
Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
Cisco ITN CCNA 1 v6.0 Chapter 5 Exam Answer R&S 2018 2019 003 - Host A sends an ARP request to the MAC address of host D.
- Host D sends an ARP request to host A.
- Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds.
- Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
Explanation:
Whenever the destination MAC address is not contained within the ARP table of the originating host, the host (host A in this example) will send a Layer 2 broadcast that has a destination MAC address of FF:FF:FF:FF:FF:FF. All devices on the same network receive this broadcast. Host D will respond to this broadcast.
-
Refer to the exhibit. The switches are in their default configuration. Host A needs to communicate with host D, but host A does not have the MAC address for its default gateway. Which network hosts will receive the ARP request sent by host A?
Cisco ITN CCNA 1 v6.0 Chapter 5 Exam Answer R&S 2018 2019 004 - only host D
- only router R1
- only hosts A, B, and C
- only hosts A, B, C, and D
- only hosts B and C
- only hosts B, C, and router R1
Explanation:
Since host A does not have the MAC address of the default gateway in its ARP table, host A sends an ARP broadcast. The ARP broadcast would be sent to every device on the local network. Hosts B, C, and router R1 would receive the broadcast. Router R1 would not forward the message.
-
Which statement describes the treatment of ARP requests on the local link?
- They must be forwarded by all routers on the local network.
- They are received and processed by every device on the local network.
- They are dropped by all switches on the local network.
- They are received and processed only by the target device.
Explanation:
One of the negative issues with ARP requests is that they are sent as a broadcast. This means all devices on the local link must receive and process the request.
-
What are two potential network problems that can result from ARP operation? (Choose two.)
- Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
- On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays.
- Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.
- Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
- Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
Explanation:
Large numbers of ARP broadcast messages could cause momentary data communications delays. Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent to intercept network traffic. ARP requests and replies cause entries to be made into the ARP table, not the MAC address table. ARP table overflows are very unlikely. Manually configuring static ARP associations is a way to prevent, not facilitate, ARP poisoning and MAC address spoofing. Multiple ARP replies resulting in the switch MAC address table containing entries that match the MAC addresses of connected nodes and are associated with the relevant switch port are required for normal switch frame forwarding operations. It is not an ARP caused network problem.
-
Fill in the blank.
A collision fragment, also known as a RUNT frame, is a frame of fewer than 64 bytes in length. -
Fill in the blank.
On a Cisco switch, port-based memory buffering is used to buffer frames in queues linked to specific incoming and outgoing ports.
-
Fill in the blank.
ARP spoofing is a technique that is used to send fake ARP messages to other hosts in the LAN. The aim is to associate IP addresses to the wrong MAC addresses. -
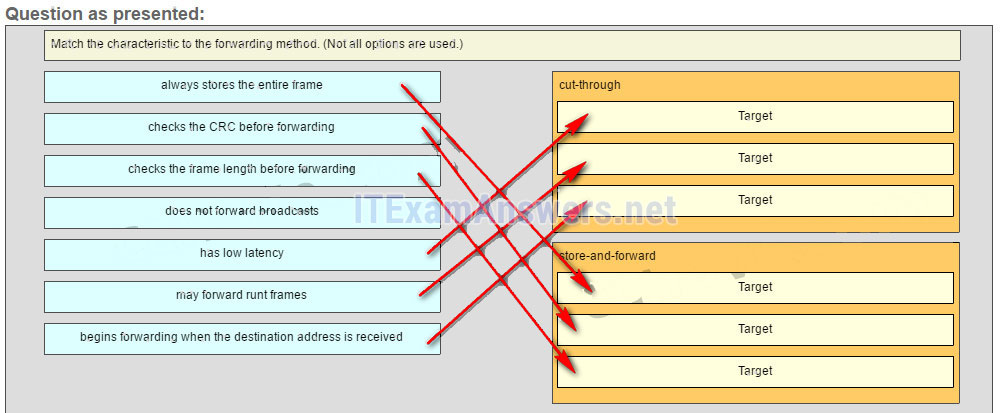
Match the characteristic to the forwarding method. (Not all options are used.)
- Question
Cisco ITN CCNA 1 v6.0 Chapter 5 Exam Answer R&S 2018 2019 005 - Answer
Cisco ITN CCNA 1 v6.0 Chapter 5 Exam Answer R&S 2018 2019 006 Explanation:A store-and-forward switch always stores the entire frame before forwarding, and checks its CRC and frame length. A cut-through switch can forward frames before receiving the destination address field, thus presenting less latency than a store-and-forward switch. Because the frame can begin to be forwarded before it is completely received, the switch may transmit a corrupt or runt frame. All forwarding methods require a Layer 2 switch to forward broadcast frames.
- Question
-
What is the minimum Ethernet frame size that will not be discarded by the receiver as a runt frame?
- 64 bytes
- 512 bytes
- 1024 bytes
- 1500 bytes
Explanation:
The minimum Ethernet frame size is 64 bytes. Frames smaller than 64 bytes are considered collision fragments or runt frames and are discarded.
-
What is a characteristic of port-based memory buffering?
- All frames are stored in a common memory buffer.
- Frames are buffered in queues linked to specific ports.
- All ports on a switch share a single memory buffer.
- Frames in the memory buffer are dynamically linked to destination ports.
Explanation:
Buffering is a technique used by Ethernet switches to store frames until they can be transmitted. With port-based buffering, frames are stored in queues that are linked to specific incoming and outgoing ports.
-
What is the aim of an ARP spoofing attack?
- to flood the network with ARP reply broadcasts
- to fill switch MAC address tables with bogus addresses
- to associate IP addresses to the wrong MAC address
- to overwhelm network hosts with ARP requests
Explanation:
In an ARP spoofing attack, a malicious host intercepts ARP requests and replies to them so that network hosts will map an IP address to the MAC address of the malicious host.
-
Recommend
31/01/2019
CCNA 1 Exam Answers, Cisco
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
- What happens to runt frames received by a Cisco Ethernet switch?
- The frame is dropped.*
- The frame is returned to the originating network device.
- The frame is broadcast to all other devices on the same network.
- The frame is sent to the default gateway.
Explain:
In an attempt to conserve bandwidth and not forward useless frames, Ethernet devices drop frames that are considered to be runt (less than 64 bytes) or jumbo (greater than 1500 bytes) frames. - What are the two sizes (minimum and maximum) of an Ethernet frame? (Choose two.)
- 56 bytes
- 64 bytes*
- 128 bytes
- 1024 bytes
- 1518 bytes*
Explain:
The minimum Ethernet frame is 64 bytes. The maximum Ethernet frame is 1518 bytes. A network technician must know the minimum and maximum frame size in order to recognize runt and jumbo frames. - What statement describes Ethernet?
- It defines the most common LAN type in the world.*
- It is the required Layer 1 and 2 standard for Internet communication.
- It defines a standard model used to describe how networking works.
- It connects multiple sites such as routers located in different countries.
Explain:
Ethernet is the most common LAN protocol in the world. It operates at Layer 1 and 2, but is not required for Internet communication. The OSI model is used to describe how networks operate. A WAN connects multiple sites located in different countries. - Which two statements describe features or functions of the logical link control sublayer in Ethernet standards? (Choose two.)
- Logical link control is implemented in software.*
- Logical link control is specified in the IEEE 802.3 standard.
- The LLC sublayer adds a header and a trailer to the data.
- The data link layer uses LLC to communicate with the upper layers of the protocol suite.*
- The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
Explain:
Logical link control is implemented in software and enables the data link layer to communicate with the upper layers of the protocol suite. Logical link control is specified in the IEEE 802.2 standard. IEEE 802.3 is a suite of standards that define the different Ethernet types. The MAC (Media Access Control) sublayer is responsible for the placement and retrieval of frames on and off the media. The MAC sublayer is also responsible for adding a header and a trailer to the network layer protocol data unit (PDU). - What statement describes a characteristic of MAC addresses?
- They must be globally unique.*
- They are only routable within the private network.
- They are added as part of a Layer 3 PDU.
- They have a 32-bit binary value.
Explain:
Any vendor selling Ethernet devices must register with the IEEE to ensure the vendor is assigned a unique 24-bit code, which becomes the first 24 bits of the MAC address. The last 24 bits of the MAC address are generated per hardware device. This helps to ensure globally unique addresses for each Ethernet device. - Which statement is true about MAC addresses?
- MAC addresses are implemented by software.
- A NIC only needs a MAC address if connected to a WAN.
- The first three bytes are used by the vendor assigned OUI.*
- The ISO is responsible for MAC addresses regulations.
Explain:
A MAC address is composed of 6 bytes. The first 3 bytes are used for vendor identification and the last 3 bytes must be assigned a unique value within the same OUI. MAC addresses are implemented in hardware. A NIC needs a MAC address to communicate over the LAN. The IEEE regulates the MAC addresses. - Which destination address is used in an ARP request frame?
- 0.0.0.0
- 255.255.255.255
- FFFF.FFFF.FFFF*
- 127.0.0.1
- 01-00-5E-00-AA-23
Explain:
The purpose of an ARP request is to find the MAC address of the destination host on an Ethernet LAN. The ARP process sends a Layer 2 broadcast to all devices on the Ethernet LAN. The frame contains the IP address of the destination and the broadcast MAC address, FFFF.FFFF.FFFF. - What addressing information is recorded by a switch to build its MAC address table?
- the destination Layer 3 address of incoming packets
- the destination Layer 2 address of outgoing frames
- the source Layer 3 address of outgoing packets
- the source Layer 2 address of incoming frames*
Explain:
A switch builds a MAC address table by inspecting incoming Layer 2 frames and recording the source MAC address found in the frame header. The discovered and recorded MAC address is then associated with the port used to receive the frame. - Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?
- The switch will discard the frame.
- The switch will forward the frame only to port 2.
- The switch will forward the frame to all ports except port 4.*
- The switch will forward the frame to all ports.
- The switch will forward the frame only to ports 1 and 3.
Explain:
The MAC address of PC3 is not present in the MAC table of the switch. Because the switch does not know where to send the frame that is addressed to PC3, it will forward the frame to all the switch ports, except for port 4, which is the incoming port. - Which switching method uses the CRC value in a frame?
- cut-through
- fast-forward
- fragment-free
- store-and-forward*
Explain:
When the store-and-forward switching method is used, the switch receives the complete frame before forwarding it on to the destination. The cyclic redundancy check (CRC) part of the trailer is used to determine if the frame has been modified during transit. In contrast, a cut-through switch forwards the frame once the destination Layer 2 address is read. Two types of cut-through switching methods are fast-forward and fragment-free. - What is auto-MDIX?
- a type of Cisco switch
- an Ethernet connector type
- a type of port on a Cisco switch
- a feature that detects Ethernet cable type*
Explain:
Auto-MDIX is a feature that is enabled on the latest Cisco switches and that allows the switch to detect and use whatever type of cable is attached to a specific port. - Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
- PC2 will send an ARP reply with its MAC address.*
- RT1 will send an ARP reply with its Fa0/0 MAC address.
- RT1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with its Fa0/1 MAC address.
Explain:
When a network device wants to communicate with another device on the same network, it sends a broadcast ARP request. In this case, the request will contain the IP address of PC2. The destination device (PC2) sends an ARP reply with its MAC address. - What is the aim of an ARP spoofing attack?
- to associate IP addresses to the wrong MAC address*
- to overwhelm network hosts with ARP requests
- to flood the network with ARP reply broadcasts
- to fill switch MAC address tables with bogus addresses
- What is a characteristic of port-based memory buffering?
- Frames in the memory buffer are dynamically linked to destination ports.
- All frames are stored in a common memory buffer.
- Frames are buffered in queues linked to specific ports.*
- All ports on a switch share a single memory buffer.
Explain:Buffering is a technique used by Ethernet switches to store frames until they can be transmitted. With port-based buffering, frames are stored in queues that are linked to specific incoming and outgoing ports. - What is the minimum Ethernet frame size that will not be discarded by the receiver as a runt frame?
- 64 bytes*
- 512 bytes
- 1024 bytes
- 1500 bytes
- What are two potential network problems that can result from ARP operation? (Choose two.)
- Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
- On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays. *
- Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.*
- Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
- Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
Explain:
Large numbers of ARP broadcast messages could cause momentary data communications delays. Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent to intercept network traffic. ARP requests and replies cause entries to be made into the ARP table, not the MAC address table. ARP table overflows are very unlikely. Manually configuring static ARP associations is a way to prevent, not facilitate, ARP poisoning and MAC address spoofing. Multiple ARP replies resulting in the switch MAC address table containing entries that match the MAC addresses of connected nodes and are associated with the relevant switch port are required for normal switch frame forwarding operations. It is not an ARP caused network problem. - Fill in the blank.
A collision fragment, also known as a RUNT frame, is a frame of fewer than 64 bytes in length.
Explain:
A runt frame is a frame of fewer than 64 bytes, usually generated by a collision or a network interface failure. - Fill in the blank.
On a Cisco switch, port-based memory buffering is used to buffer frames in queues linked to specific incoming and outgoing ports. - Fill in the blank.
ARP spoofing is a technique that is used to send fake ARP messages to other hosts in the LAN. The aim is to associate IP addresses to the wrong MAC addresses.
Explain:
ARP spoofing or ARP poisoning is a technique used by an attacker to reply to an ARP request for an IPv4 address belonging to another device, such as the default gateway. - Which statement describes the treatment of ARP requests on the local link?
They must be forwarded by all routers on the local network.
They are received and processed by every device on the local network.*
They are dropped by all switches on the local network.
They are received and processed only by the target device. - Refer to the exhibit.
The switches are in their default configuration. Host A needs to communicate with host D, but host A does not have the MAC address for its default gateway. Which network hosts will receive the ARP request sent by host A?
only host D
only router R1
only hosts A, B, and C
only hosts A, B, C, and D
only hosts B and C
only hosts B, C, and router R1*
Explain:
Since host A does not have the MAC address of the default gateway in its ARP table, host A sends an ARP broadcast. The ARP broadcast would be sent to every device on the local network. Hosts B, C, and router R1 would receive the broadcast. Router R1 would not forward the message. - Refer to the exhibit.
A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?Host A sends an ARP request to the MAC address of host D.
Host D sends an ARP request to host A.
Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds.
Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.*
Explain:
Whenever the destination MAC address is not contained within the ARP table of the originating host, the host (host A in this example) will send a Layer 2 broadcast that has a destination MAC address of FF:FF:FF:FF:FF:FF. All devices on the same network receive this broadcast. Host D will respond to this broadcast. - True or False?
When a device is sending data to another device on a remote network, the Ethernet frame is sent to the MAC address of the default gateway.
true*
false
Explain:
A MAC address is only useful on the local Ethernet network. When data is destined for a remote network of any type, the data is sent to the default gateway device, the Layer 3 device that routes for the local network. - The ARP table in a switch maps which two types of address together?
Layer 3 address to a Layer 2 address*
Layer 3 address to a Layer 4 address
Layer 4 address to a Layer 2 address
Layer 2 address to a Layer 4 address
Explain:
The switch ARP table keeps a mapping of Layer 2 MAC addresses to Layer 3 IP addresses. These mappings can be learned by the switch dynamically through ARP or statically through manual configuration. - Match the characteristic to the forwarding method. (Not all options are used.)
Sort elements
cut-through (A) -> low latency (A)*
cut-through (B) -> may forward runt frames (B)*
cut-through (C) -> begins forwarding when the destination address is received (C)*
store-and-forward (D) -> always stores the entire frame (D)*
store-and-forward (E) -> checks the CRC before forwarding (E)*
store-and-forward (F) -> checks the frame length before forwarding (F)
Explain:
A store-and-forward switch always stores the entire frame before forwarding, and checks its CRC and frame length. A cut-through switch can forward frames before receiving the destination address field, thus presenting less latency than a store-and-forward switch. Because the frame can begin to be forwarded before it is completely received, the switch may transmit a corrupt or runt frame. All forwarding methods require a Layer 2 switch to forward broadcast frames.
Other Questions
- What is a characteristic of a contention-based access method?
- It processes more overhead than the controlled access methods do.
- It has mechanisms to track the turns to access the media.
- It is a nondeterministic method.*
- It scales very well under heavy media use.
- What is the purpose of the preamble in an Ethernet frame?
- is used as a padding for data
- is used for timing synchronization*
- is used to identify the source address
- is used to identify the destination address
- What is the Layer 2 multicast MAC address that corresponds to the Layer 3 IPv4 multicast address 224.139.34.56?
- 00-00-00-0B-22-38
- 01-00-5E-0B-22-38*
- 01-5E-00-0B-22-38
- FE-80-00-0B-22-38
- FF-FF-FF-0B-22-38
- Which two statements are correct about MAC and IP addresses during data transmission if NAT is not involved? (Choose two.)
- A packet that has crossed four routers has changed the destination IP address four times.
- Destination MAC addresses will never change in a frame that goes across seven routers.
- Destination and source MAC addresses have local significance and change every time a frame goes from one LAN to another. *
- Destination IP addresses in a packet header remain constant along the entire path to a target host.*
- Every time a frame is encapsulated with a new destination MAC address, a new destination IP address is needed.
- What are two features of ARP? (Choose two.)
- If a host is ready to send a packet to a local destination device and it has the IP address but not the MAC address of the destination, it generates an ARP broadcast.*
- An ARP request is sent to all devices on the Ethernet LAN and contains the IP address of the destination host and its multicast MAC address.
- When a host is encapsulating a packet into a frame, it refers to the MAC address table to determine the mapping of IP addresses to MAC addresses.
- If no device responds to the ARP request, then the originating node will broadcast the data packet to all devices on the network segment.
- If a device receiving an ARP request has the destination IPv4 address, it responds with an ARP reply.*
- A host is trying to send a packet to a device on a remote LAN segment, but there are currently no mappings in its ARP cache. How will the device obtain a destination MAC address?
- It will send an ARP request for the MAC address of the destination device.
- It will send an ARP request for the MAC address of the default gateway. *
- It will send the frame and use its own MAC address as the destination. *
- It will send the frame with a broadcast MAC address.
- It will send a request to the DNS server for the destination MAC address.
- A network administrator is connecting two modern switches using a straight-through cable. The switches are new and have never been configured. Which three statements are correct about the final result of the connection? (Choose three.)
- The link between the switches will work at the fastest speed that is supported by both switches. *
- The link between switches will work as full-duplex.*
- If both switches support different speeds, they will each work at their own fastest speed.
- The auto-MDIX feature will configure the interfaces eliminating the need for a crossover cable.*
- The connection will not be possible unless the administrator changes the cable to a crossover cable.
- The duplex capability has to be manually configured because it cannot be negotiated.
- A Layer 2 switch is used to switch incoming frames from a 1000BASE-T port to a port connected to a 100Base-T network. Which method of memory buffering would work best for this task?
- port-based buffering
- level 1 cache buffering
- shared memory buffering*
- fixed configuration buffering
- When would a switch record multiple entries for a single switch port in its MAC address table?
- when a router is connected to the switch port
- when multiple ARP broadcasts have been forwarded
- when another switch is connected to the switch port*
- when the switch is configured for Layer 3 switching
- Which two statements describe a fixed configuration Ethernet switch? (Choose two.)
- The switch cannot be configured with multiple VLANs.
- An SVI cannot be configured on the switch.
- A fixed configuration switch may be stackable. *
- The number of ports on the switch cannot be increased.*
- The port density of the switch is determined by the Cisco IOS.
- How does adding an Ethernet line card affect the form factor of a switch?
- by increasing the back plane switching speed
- by expanding the port density*
- by making the switch stackable
- by expanding the NVRAM capacity
- Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
- IP address only
- port address only
- MAC address only
- MAC and port addresses
- MAC and IP addresses*
- What statement illustrates a drawback of the CSMA/CD access method?
- Deterministic media access protocols slow network performance.
- It is more complex than non-deterministic protocols.
- Collisions can decrease network performance.*
- CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
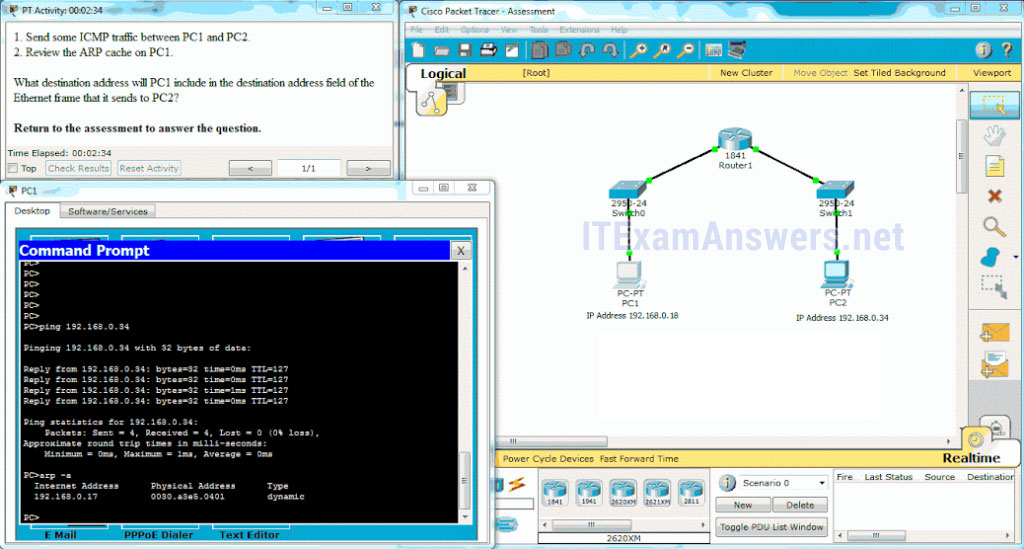
- Open the PT Activity. Perform the tasks in the activity instruction and then answer the question.
What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?- 192.168.0.17
- 192.168.0.34
- 0030.a3e5.0401*
- 00e0.b0be.8014
- 0007.ec35.a5c6
- Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
- MAC and IP addresses*
- MAC address only
- MAC and port addresses
- port address only
- IP address only
- Launch PT. Hide and Save PT
Open the PT Activity. Perform the tasks in the activity instruction and then answer the question. What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?- 00e0.b0be.8014
- 0030.a3e5.0401*
- 192.168.0.34
- 192.168.0.17
- 0007.ec35.a5c6
- How does adding an Ethernet line card affect the form factor of a switch?
- by increasing the back plane switching speed
- by expanding the port density*
- by expanding the NVRAM capacity
- by making the switch stackable
- What statement illustrates a drawback of the CSMA/CD access method?
- Collisions can decrease network performance.*
- Deterministic media access protocols slow network performance.
- CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
- It is more complex than non-deterministic protocols.
- A network administrator issues the following commands on a Layer 3 switch:
DLS1(config)# interface f0/3 DLS1(config-if)# no switchport DLS1(config-if)# ip address 172.16.0.1 255.255.255.0 DLS1(config-if)# no shutdown DLS1(config-if)# end
What is the administrator configuring?
- a Cisco Express Forwarding instance
- a routed port*
- a trunk interface
- a switched virtual interface
- The binary number 0000 1010 can be expressed as “A” in hexadecimal.
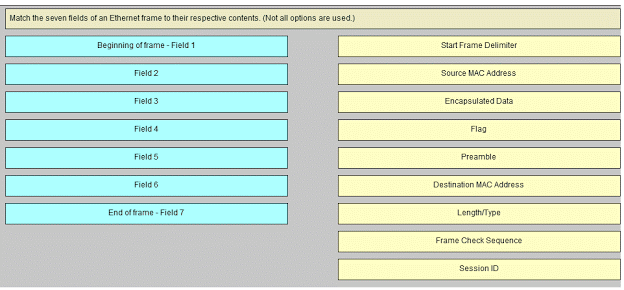
Match the seven fields of an Ethernet frame to their respective contents. (Not all options are used.)
Sort elements
Start Frame Delimiter -> Field 2*
Source MAC Address -> Field 4*
Encapsulated Data -> Field 6*
Preamble -> Beginning of frame – Field 1*
Destination MAC Address -> Field 3*
Length/Type -> Field 5*
Frame Check Sequence -> End of frame – Field 7
Download PDF File below:
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
1. What happens to runt frames received by a Cisco Ethernet switch?
- The frame is dropped.
- The frame is returned to the originating network device.
- The frame is broadcast to all other devices on the same network.
- The frame is sent to the default gateway.
Explain:
In an attempt to conserve bandwidth and not forward useless frames, Ethernet devices drop frames that are considered to be runt (less than 64 bytes) or jumbo (greater than 1500 bytes) frames.
2. What are the two sizes (minimum and maximum) of an Ethernet frame? (Choose two.)
- 56 bytes
- 64 bytes
- 128 bytes
- 1024 bytes
- 1518 bytes
Explain:
The minimum Ethernet frame is 64 bytes. The maximum Ethernet frame is 1518 bytes. A network technician must know the minimum and maximum frame size in order to recognize runt and jumbo frames.
3. What statement describes Ethernet?
- It defines the most common LAN type in the world.
- It is the required Layer 1 and 2 standard for Internet communication.
- It defines a standard model used to describe how networking works.
- It connects multiple sites such as routers located in different countries.
Explain:
Ethernet is the most common LAN protocol in the world. It operates at Layer 1 and 2, but is not required for Internet communication. The OSI model is used to describe how networks operate. A WAN connects multiple sites located in different countries.
4. Which two statements describe features or functions of the logical link control sublayer in Ethernet standards? (Choose two.)
- Logical link control is implemented in software.
- Logical link control is specified in the IEEE 802.3 standard.
- The LLC sublayer adds a header and a trailer to the data.
- The data link layer uses LLC to communicate with the upper layers of the protocol suite.
- The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
Explain:
Logical link control is implemented in software and enables the data link layer to communicate with the upper layers of the protocol suite. Logical link control is specified in the IEEE 802.2 standard. IEEE 802.3 is a suite of standards that define the different Ethernet types. The MAC (Media Access Control) sublayer is responsible for the placement and retrieval of frames on and off the media. The MAC sublayer is also responsible for adding a header and a trailer to the network layer protocol data unit (PDU).
5. What statement describes a characteristic of MAC addresses?
- They must be globally unique.
- They are only routable within the private network.
- They are added as part of a Layer 3 PDU.
- They have a 32-bit binary value.
Explain:
Any vendor selling Ethernet devices must register with the IEEE to ensure the vendor is assigned a unique 24-bit code, which becomes the first 24 bits of the MAC address. The last 24 bits of the MAC address are generated per hardware device. This helps to ensure globally unique addresses for each Ethernet device.
6. Which statement is true about MAC addresses?
- MAC addresses are implemented by software.
- A NIC only needs a MAC address if connected to a WAN.
- The first three bytes are used by the vendor assigned OUI.
- The ISO is responsible for MAC addresses regulations.
Explain:
A MAC address is composed of 6 bytes. The first 3 bytes are used for vendor identification and the last 3 bytes must be assigned a unique value within the same OUI. MAC addresses are implemented in hardware. A NIC needs a MAC address to communicate over the LAN. The IEEE regulates the MAC addresses.
7. Which destination address is used in an ARP request frame?
- 0.0.0.0
- 255.255.255.255
- FFFF.FFFF.FFFF
- 127.0.0.1
- 01-00-5E-00-AA-23
Explain:
The purpose of an ARP request is to find the MAC address of the destination host on an Ethernet LAN. The ARP process sends a Layer 2 broadcast to all devices on the Ethernet LAN. The frame contains the IP address of the destination and the broadcast MAC address, FFFF.FFFF.FFFF.
8. What addressing information is recorded by a switch to build its MAC address table?
- the destination Layer 3 address of incoming packets
- the destination Layer 2 address of outgoing frames
- the source Layer 3 address of outgoing packets
- the source Layer 2 address of incoming frames
Explain:
A switch builds a MAC address table by inspecting incoming Layer 2 frames and recording the source MAC address found in the frame header. The discovered and recorded MAC address is then associated with the port used to receive the frame.
9. Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?
- The switch will discard the frame.
- The switch will forward the frame only to port 2.
- The switch will forward the frame to all ports except port 4.
- The switch will forward the frame to all ports.
- The switch will forward the frame only to ports 1 and 3.
Explain:
The MAC address of PC3 is not present in the MAC table of the switch. Because the switch does not know where to send the frame that is addressed to PC3, it will forward the frame to all the switch ports, except for port 4, which is the incoming port.
10. Which switching method uses the CRC value in a frame?
- cut-through
- fast-forward
- fragment-free
- store-and-forward
Explain:
When the store-and-forward switching method is used, the switch receives the complete frame before forwarding it on to the destination. The cyclic redundancy check (CRC) part of the trailer is used to determine if the frame has been modified during transit. In contrast, a cut-through switch forwards the frame once the destination Layer 2 address is read. Two types of cut-through switching methods are fast-forward and fragment-free.
11. What is auto-MDIX?
- a type of Cisco switch
- an Ethernet connector type
- a type of port on a Cisco switch
- a feature that detects Ethernet cable type
Explain:
Auto-MDIX is a feature that is enabled on the latest Cisco switches and that allows the switch to detect and use whatever type of cable is attached to a specific port.
12. Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
- PC2 will send an ARP reply with its MAC address.
- RT1 will send an ARP reply with its Fa0/0 MAC address.
- RT1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with its Fa0/1 MAC address.
Explain:
When a network device wants to communicate with another device on the same network, it sends a broadcast ARP request. In this case, the request will contain the IP address of PC2. The destination device (PC2) sends an ARP reply with its MAC address.
13. What is the aim of an ARP spoofing attack?
- to associate IP addresses to the wrong MAC address
- to overwhelm network hosts with ARP requests
- to flood the network with ARP reply broadcasts
- to fill switch MAC address tables with bogus addresses
Explanation: In an ARP spoofing attack, a malicious host intercepts ARP requests and replies to them so that network hosts will map an IP address to the MAC address of the malicious host.
14. What is a characteristic of port-based memory buffering?
- Frames in the memory buffer are dynamically linked to destination ports.
- All frames are stored in a common memory buffer.
- Frames are buffered in queues linked to specific ports.
- All ports on a switch share a single memory buffer.
Explain:Buffering is a technique used by Ethernet switches to store frames until they can be transmitted. With port-based buffering, frames are stored in queues that are linked to specific incoming and outgoing ports.
15. What is the minimum Ethernet frame size that will not be discarded by the receiver as a runt frame?
- 64 bytes
- 512 bytes
- 1024 bytes
- 1500 bytes
16. What are two potential network problems that can result from ARP operation? (Choose two.)
- Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
- On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays.
- Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.
- Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
- Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
Explain:
Large numbers of ARP broadcast messages could cause momentary data communications delays. Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent to intercept network traffic. ARP requests and replies cause entries to be made into the ARP table, not the MAC address table. ARP table overflows are very unlikely. Manually configuring static ARP associations is a way to prevent, not facilitate, ARP poisoning and MAC address spoofing. Multiple ARP replies resulting in the switch MAC address table containing entries that match the MAC addresses of connected nodes and are associated with the relevant switch port are required for normal switch frame forwarding operations. It is not an ARP caused network problem.
17. Fill in the blank.
A collision fragment, also known as a RUNT frame, is a frame of fewer than 64 bytes in length.
Explain:
A runt frame is a frame of fewer than 64 bytes, usually generated by a collision or a network interface failure.
18. Fill in the blank.
On a Cisco switch, port-based memory buffering is used to buffer frames in queues linked to specific incoming and outgoing ports.
19. Fill in the blank.
ARP spoofing is a technique that is used to send fake ARP messages to other hosts in the LAN. The aim is to associate IP addresses to the wrong MAC addresses.
Explain:
ARP spoofing or ARP poisoning is a technique used by an attacker to reply to an ARP request for an IPv4 address belonging to another device, such as the default gateway.
20. Which statement describes the treatment of ARP requests on the local link?
- They must be forwarded by all routers on the local network.
- They are received and processed by every device on the local network.
- They are dropped by all switches on the local network.
- They are received and processed only by the target device.
21. Refer to the exhibit. The switches are in their default configuration. Host A needs to communicate with host D, but host A does not have the MAC address for its default gateway. Which network hosts will receive the ARP request sent by host A?
- only host D
- only router R1
- only hosts A, B, and C
- only hosts A, B, C, and D
- only hosts B and C
- only hosts B, C, and router R1
Explain:
Since host A does not have the MAC address of the default gateway in its ARP table, host A sends an ARP broadcast. The ARP broadcast would be sent to every device on the local network. Hosts B, C, and router R1 would receive the broadcast. Router R1 would not forward the message.
22. Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
- Host A sends an ARP request to the MAC address of host D.
- Host D sends an ARP request to host A.
- Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds.
- Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
Explain:
Whenever the destination MAC address is not contained within the ARP table of the originating host, the host (host A in this example) will send a Layer 2 broadcast that has a destination MAC address of FF:FF:FF:FF:FF:FF. All devices on the same network receive this broadcast. Host D will respond to this broadcast.
23. True or False?
When a device is sending data to another device on a remote network, the Ethernet frame is sent to the MAC address of the default gateway.
- true
- false
Explain:
A MAC address is only useful on the local Ethernet network. When data is destined for a remote network of any type, the data is sent to the default gateway device, the Layer 3 device that routes for the local network.
24. The ARP table in a switch maps which two types of address together?
- Layer 3 address to a Layer 2 address
- Layer 3 address to a Layer 4 address
- Layer 4 address to a Layer 2 address
- Layer 2 address to a Layer 4 address
Explain:
The switch ARP table keeps a mapping of Layer 2 MAC addresses to Layer 3 IP addresses. These mappings can be learned by the switch dynamically through ARP or statically through manual configuration.
25. Match the characteristic to the forwarding method. (Not all options are used.)
Explain: A store-and-forward switch always stores the entire frame before forwarding, and checks its CRC and frame length. A cut-through switch can forward frames before receiving the destination address field, thus presenting less latency than a store-and-forward switch. Because the frame can begin to be forwarded before it is completely received, the switch may transmit a corrupt or runt frame. All forwarding methods require a Layer 2 switch to forward broadcast frames.
Other Questions
26. What is a characteristic of a contention-based access method?
- It processes more overhead than the controlled access methods do.
- It has mechanisms to track the turns to access the media.
- It is a nondeterministic method.
- It scales very well under heavy media use.
27. What is the purpose of the preamble in an Ethernet frame?
- is used as a padding for data
- is used for timing synchronization
- is used to identify the source address
- is used to identify the destination address
28. What is the Layer 2 multicast MAC address that corresponds to the Layer 3 IPv4 multicast address 224.139.34.56?
- 00-00-00-0B-22-38
- 01-00-5E-0B-22-38
- 01-5E-00-0B-22-38
- FE-80-00-0B-22-38
- FF-FF-FF-0B-22-38
29. Which two statements are correct about MAC and IP addresses during data transmission if NAT is not involved? (Choose two.)
- A packet that has crossed four routers has changed the destination IP address four times.
- Destination MAC addresses will never change in a frame that goes across seven routers.
- Destination and source MAC addresses have local significance and change every time a frame goes from one LAN to another.
- Destination IP addresses in a packet header remain constant along the entire path to a target host.
- Every time a frame is encapsulated with a new destination MAC address, a new destination IP address is needed.
30. What are two features of ARP? (Choose two.)
- If a host is ready to send a packet to a local destination device and it has the IP address but not the MAC address of the destination, it generates an ARP broadcast.
- An ARP request is sent to all devices on the Ethernet LAN and contains the IP address of the destination host and its multicast MAC address.
- When a host is encapsulating a packet into a frame, it refers to the MAC address table to determine the mapping of IP addresses to MAC addresses.
- If no device responds to the ARP request, then the originating node will broadcast the data packet to all devices on the network segment.
- If a device receiving an ARP request has the destination IPv4 address, it responds with an ARP reply.
31. A host is trying to send a packet to a device on a remote LAN segment, but there are currently no mappings in its ARP cache. How will the device obtain a destination MAC address?
- It will send an ARP request for the MAC address of the destination device.
- It will send an ARP request for the MAC address of the default gateway.
- It will send the frame and use its own MAC address as the destination.
- It will send the frame with a broadcast MAC address.
- It will send a request to the DNS server for the destination MAC address.
32. A network administrator is connecting two modern switches using a straight-through cable. The switches are new and have never been configured. Which three statements are correct about the final result of the connection? (Choose three.)
- The link between the switches will work at the fastest speed that is supported by both switches.
- The link between switches will work as full-duplex.
- If both switches support different speeds, they will each work at their own fastest speed.
- The auto-MDIX feature will configure the interfaces eliminating the need for a crossover cable.
- The connection will not be possible unless the administrator changes the cable to a crossover cable.
- The duplex capability has to be manually configured because it cannot be negotiated.
33. A Layer 2 switch is used to switch incoming frames from a 1000BASE-T port to a port connected to a 100Base-T network. Which method of memory buffering would work best for this task?
- port-based buffering
- level 1 cache buffering
- shared memory buffering
- fixed configuration buffering
34. When would a switch record multiple entries for a single switch port in its MAC address table?
- when a router is connected to the switch port
- when multiple ARP broadcasts have been forwarded
- when another switch is connected to the switch port
- when the switch is configured for Layer 3 switching
Explanation: When another switch or a hub is connected to a switch port then frames could be received from the multiple nodes connected to the other switch or the hub. This will result in the MAC address for each of those multiple nodes to be recorded in the MAC address table against that one port. When a router is connected to a switch port, only the MAC address of the router interface would be recorded against the switch port. ARP broadcasts are used to associate MAC addresses with IP addresses and such broadcasts would not directly result in multiple MAC addresses being recorded against a single switch port. Configuring the switch to perform Layer 3 switching will not result in multiple MAC addresses being recorded against a single switch port. The ARP table associated with the Layer 3 switch port may contain multiple IP address to MAC address mappings but this is to enable the correct framing of Layer 3 packets, not the Layer 2 frame switching function.
35. Which two statements describe a fixed configuration Ethernet switch? (Choose two.)
- The switch cannot be configured with multiple VLANs.
- An SVI cannot be configured on the switch.
- A fixed configuration switch may be stackable.
- The number of ports on the switch cannot be increased.
- The port density of the switch is determined by the Cisco IOS.
36. How does adding an Ethernet line card affect the form factor of a switch?
- by increasing the back plane switching speed
- by expanding the port density
- by making the switch stackable
- by expanding the NVRAM capacity
37. Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
- IP address only
- port address only
- MAC address only
- MAC and port addresses
- MAC and IP addresses
38. What statement illustrates a drawback of the CSMA/CD access method?
- Deterministic media access protocols slow network performance.
- It is more complex than non-deterministic protocols.
- Collisions can decrease network performance.
- CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
39. Open the PT Activity. Perform the tasks in the activity instruction and then answer the question.
What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?
- 192.168.0.17
- 192.168.0.34
- 0030.a3e5.0401
- 00e0.b0be.8014
- 0007.ec35.a5c6
40. Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
- MAC and IP addresses
- MAC address only
- MAC and port addresses
- port address only
- IP address only
41. Launch PT. Hide and Save PT
Open the PT Activity. Perform the tasks in the activity instruction and then answer the question. What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?
- 00e0.b0be.8014
- 0030.a3e5.0401
- 192.168.0.34
- 192.168.0.17
- 0007.ec35.a5c6
42. How does adding an Ethernet line card affect the form factor of a switch?
- by increasing the back plane switching speed
- by expanding the port density
- by expanding the NVRAM capacity
- by making the switch stackable
43. What statement illustrates a drawback of the CSMA/CD access method?
- Collisions can decrease network performance.
- Deterministic media access protocols slow network performance.
- CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
- It is more complex than non-deterministic protocols.
44. A network administrator issues the following commands on a Layer 3 switch:
DLS1(config)# interface f0/3 DLS1(config-if)# no switchport DLS1(config-if)# ip address 172.16.0.1 255.255.255.0 DLS1(config-if)# no shutdown DLS1(config-if)# end
What is the administrator configuring?
- a Cisco Express Forwarding instance
- a routed port
- a trunk interface
- a switched virtual interface
45. The binary number 0000 1010 can be expressed as “A” in hexadecimal.
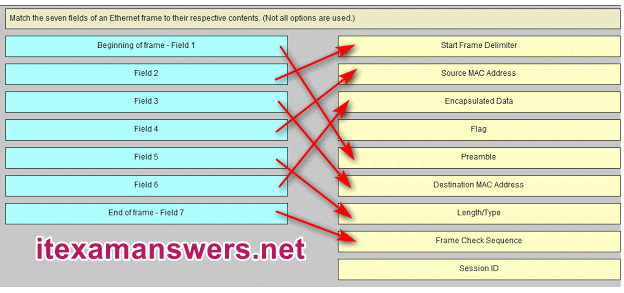
Match the seven fields of an Ethernet frame to their respective contents. (Not all options are used.)
Sort elements
Start Frame Delimiter -> Field 2*
Source MAC Address -> Field 4*
Encapsulated Data -> Field 6*
Preamble -> Beginning of frame – Field 1*
Destination MAC Address -> Field 3*
Length/Type -> Field 5*
Frame Check Sequence -> End of frame – Field 7
Download PDF File below:
[sociallocker id=”54558″]
[/sociallocker]
Last Updated on January 14, 2021 by
This quiz covers the content in CCNA R&S Introduction to Networks Chapter 5. It is designed to provide an additional opportunity to practice the skills and knowledge presented in the chapter and to prepare for the Chapter Exam.
-
Refer to the graphic. H2 has sent a broadcast message to all of the hosts. If host H1 wants to reply to the broadcast message, which statement is true?
ITN Chapter 5 Quiz Answers 02
- H1 sends a unicast message to H2, but the switch forwards it to all devices.
- H1 sends a unicast message to H2, and the switch forwards it directly to H2.
- H1 sends a broadcast message to H2, and the switch forwards it to all devices.
- H1 sends a multicast message to H2, and the switch forwards it directly to H2.
Explanation:
-
What is the decimal equivalent of the hexadecimal value of 3F?
- 18
- 34
- 45
- 46
- 63
Explanation:
-
Fill in the blank using a number.
The minimum Ethernet frame size is 64 bytes. Anything smaller than that should be considered a “runt frame.”
Explanation:
-
What is the primary purpose of ARP?
- translate URLs to IP addresses
- resolve IPv4 addresses to MAC addresses
- provide dynamic IP configuration to network devices
- convert internal private addresses to external public addresses
-
Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC3. In this scenario, what will happen next?
ITN Chapter 5 Quiz Answers 01
- RT1 will forward the ARP request to PC3.
- RT1 will send an ARP reply with its own Fa0/0 MAC address.
- RT1 will send an ARP reply with the PC3 MAC address.
- SW1 will send an ARP reply with its Fa0/1 MAC address.
- RT1 will send an ARP reply with its own Fa0/1 MAC address.
Explanation:
-
Which action is taken by a Layer 2 switch when it receives a Layer 2 broadcast frame?
- It drops the frame.
- It sends the frame to all ports except the port on which it received the frame.
- It sends the frame to all ports that are registered to forward broadcasts.
- It sends the frame to all ports.
Explanation:
-
Fill in the blank.
On Ethernet networks, the hexadecimal address FF-FF-FF-FF-FF-FF represents the broadcast MAC address.
- Noted: There are 3 possible answers. You can fill in one of the following in netacad: broadcast, Broadcast, BROADCAST. But you can fill only broadcast in our system.
Explanation:
- Noted: There are 3 possible answers. You can fill in one of the following in netacad: broadcast, Broadcast, BROADCAST. But you can fill only broadcast in our system.
-
When the store-and-forward method of switching is in use, what part of the Ethernet frame is used to perform an error check?
- CRC in the trailer
- source MAC address in the header
- destination MAC address in the header
- protocol type in the header
Explanation:
-
Which two functions or operations are performed by the MAC sublayer? (Choose two.)
- It is responsible for Media Access Control.
- It performs the function of NIC driver software.
- It adds a header and trailer to form an OSI Layer 2 PDU.
- It handles communication between upper and lower layers.
- It adds control information to network protocol layer data.
Explanation:
-
Fill in the blank.
The Ethernet MAC sublayer is responsible for communicating directly with the physical layer.
- Noted: There are 3 possible answers. You can fill in one of the following in netacad: MAC, Mac, mac. But you can fill only MAC in our system.
Explanation:
- Noted: There are 3 possible answers. You can fill in one of the following in netacad: MAC, Mac, mac. But you can fill only MAC in our system.
-
Refer to the exhibit. What is the destination MAC address of the Ethernet frame as it leaves the web server if the final destination is PC1?
ITN Chapter 5 Quiz Answers 03
- 00-60-2F-3A-07-AA
- 00-60-2F-3A-07-BB
- 00-60-2F-3A-07-CC
- 00-60-2F-3A-07-DD
Explanation:
-
Fill in the blank.
The binary number 0000 1010 can be expressed as 0A in hexadecimal.
- Noted: There are 6 possible answers. You can fill in one of the following in netacad: 0A, 0a, A, a, 0x0a, and 0x0A. But you can fill only 0A in our system.
Explanation:
- Noted: There are 6 possible answers. You can fill in one of the following in netacad: 0A, 0a, A, a, 0x0a, and 0x0A. But you can fill only 0A in our system.
-
A Layer 2 switch is used to switch incoming frames from a 1000BASE-T port to a port connected to a 100Base-T network. Which method of memory buffering would work best for this task?
- port-based buffering
- level 1 cache buffering
- shared memory buffering
- fixed configuration buffering
Explanation:
-
What type of address is 01-00-5E-0A-00-02?
- an address that reaches every host inside a local subnet
- an address that reaches one specific host
- an address that reaches every host in the network
- an address that reaches a specific group of hosts
Explanation:
-
When a switch configuration includes a user-defined error threshold on a per-port basis, to which switching method will the switch revert when the error threshold is reached?
- fragment-free
- fast-forward
- cut-through
- store-and-forward
Explanation:
Ссылка: ymyryg.ru/torrent-file-TnkwdGJxbzBqMmxNanY1SFo2aTlQcnRmcnMwbWdKTEppL2pUQnRUVW9CeGVYK3krK2F2aHRsL0lWYWZBZjJRd1hBL3FqMGFPQmIxUk4wNkFuUEx1Z2lmejFPT2tGWmtERDhSK1hDZ0c3ZHRoTlVBS1QvcHlYdHJOZTBoRnJZYUhSWlVFUG90WDlBK1duQ3l3RXM1N282akNpU3IwZ3VLL0JocnJLWXNqWXhIUytJUEpLY05rNkxaM1ZnRm40RmNi.torrent
Jun 4, 2019 what two functions describe uses of an access control list? which two statements describe the effect of the access control list wildcard mask. Сетевая академия cisco, обучение, курсы ccna, ccnp: сетевое оборудование, все ли выпускники сетевой академии cisco успешно сдают экзамены и работы по методикам cisco и сдают промежуточные тесты по этой главе. дней, а более трудный курс ccnp за 22,5 месяца (очное обучение). Jun 4, 2019 what two functions describe uses of an access control list? which two statements describe the effect of the access control list wildcard mask. 8 янв 2019 глава 2 операционные системы что во время экзамена в школе встречаются вопросы ответы на которые есть в подсказках в курсе.
экзамен по главе 5 курса itn ответы — онлайн тест — Аетерна
Cisco экзамен по главе 2 курса itn ответы экзамен по главе 1 курса itn int-ion to networks(верс. Сетевая академия cisco, обучение, курсы ccna, ccnp: сетевое оборудование, все ли выпускники сетевой академии cisco успешно сдают экзамены и работы по методикам cisco и сдают промежуточные тесты по этой главе. дней, а более трудный курс ccnp за 22,5 месяца (очное обучение). 2 какие две части являются компонентами адреса ipv4? (выберите два варианта ответа. 8 янв 2019 глава 2 операционные системы что во время экзамена в школе встречаются вопросы ответы на которые есть в подсказках в курсе.
экзамен по главе 2 курса itn ответы
Носков самоучитель немецкого языка электросхема ваз 21124 16 клапанов как научить ребенка самостоятельности экзамен по главе 5 курса itn ответы. Экзамен по главе 1 курса itn int-ion to networks(верс. Экзамен по главе 1 курса itn int-ion to networks(верс. В экзаменационных тестах от 60 до 90 вопросов с несколькими вариантами ответов. Продолжительность экзаменов от 1 до 3 часов. В экзаменационных тестах от 60 до 90 вопросов с несколькими вариантами ответов. Продолжительность экзаменов от 1 до 3 часов.
Лекция 3. Уровень приложений.
3.1 Приложения
Уровень приложений является интерфейсом между приложениями и коммуникационным ПО, так же определяет процесс аутентификации пользователя.
Функции уровня представления:
— Преобразование данных в формат понятный получателю
— Компрессия
— Шифрование
Сеансовый уровень отвечает за установление и поддерживание сеансов связи между приложениями.
Приложения можно разделить на:
— напрямую работающие сетью (Network-Aware)
— использующие для работы с сетью другие приложения (службы, демоны)
3.2 Приложения и службы
Клиент/серверная модель — в сети имеется выделенный сервер обслуживающий запросы, и клиент обращающийся к серверу.
Одноранговая (peer-to-peer) модель — компьютеры в сети выполняют как функции клиента так и функции сервера.
Peer-to-peer приложение — приложение работающее как клиент и как сервер одновременно в пределах соединения.
3.3 Примеры протоколов и служб
— Система доменных имен (DNS) — TCP/UDP порт 53. Система распределенных серверов позволяющая определять IP-адрес по доменному имени и наоборот.
nslookup программа позволяющая отправлять запросы DNS серверу.
Все сообщения DNS имеют одинаковый формат.
— Протокол передачи гипертекста (HTTP) — TCP порт 80. Протокол доступа к веб-сайтам.
Методы GET (запрос данных с сервера), POST и PUT (загрузка данных на сервер).
Главное различие методов PUT и POST в том, что при методе POST, предполагается, что по указанному URI, будет производиться обработка, передаваемых клиентом данных, а при методеPUT, клиент подразумевает, что загружаемые данные уже соответствуют ресурсу, расположенному по данному URI.
HTTPS TCP порт 443, защищенная версия протокола HTTP.
— MUA почтовый агент запрашивающий почту с сервера по протоколу POP (TCP 110) или IMAP (TCP 143) и отправляющий почту на сервер по протоколу SMTP (TCP 25).
— MTA сервис сервера почты отвечающий за пересылку почты между серверами по протоколу SMTP.
— MDA сервис сервера почты отвечающий за фильтрацию почты и размещение писем ящики пользователей
Команды SMTP: HELO, EHLO, MAIL FROM, RCPT TO, DATA.
Команды POP3: USER, PASS, LIST, RETR.
— Протокол передачи файлов (FTP) — TCP порт 21 управляющее соединение, TCP порт 20 соединение для передачи данных. Режимы работы:
— активный, клиент открывает соединение к серверу, сервер обратное соединение к клиенту (nat и firewall мешают такому режиму работы)
— пассивный, клиент открывает оба соединения к серверу самостоятельно.
— Протокол динамической настройки узлов (DHCP) UDP 67. Используется для автоматической выдачи узлам сетевых настроек. Получение настроек проходит в 4 этапа:
— DHCP Discover (клиент опрашивает сеть в поисках сервера)
— DHCP Offer (серверы отвечают клиенту)
— DHCP Request (клиент выбирает сервер и всем об этом сообщает)
— DHCP Acknowledge (сервер резервирует и передает клиенту адрес и настройки)
— SMB TCP 445 протокол позволяющий передавать файлы по сети, предоставлять принтеры в доступ другим пользователям сети.
— P2P приложения позволяют обмениваться файлами по сети.
— TELNET TCP 23, предоставляет доступ к командной строке удаленных сетевых устройств.
— SSH TCP 22, предоставляет доступ к командной строке удаленных сетевых устройств. Так же может передавать файлы и запускать графические приложения. Использует шифрование.

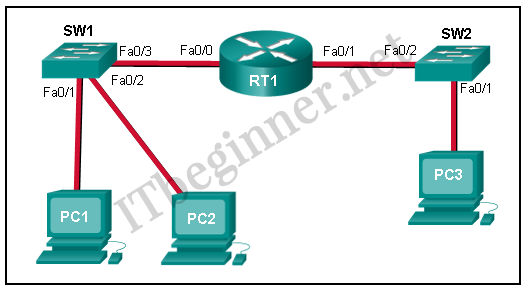
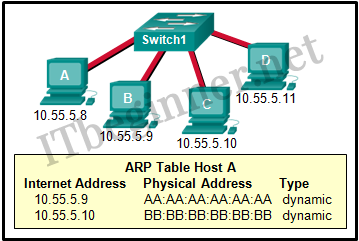
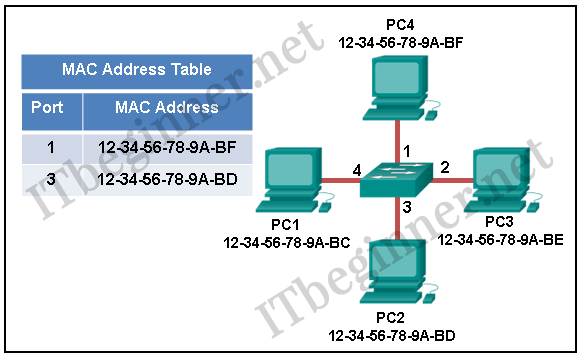
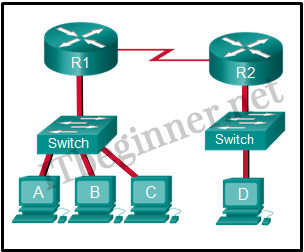






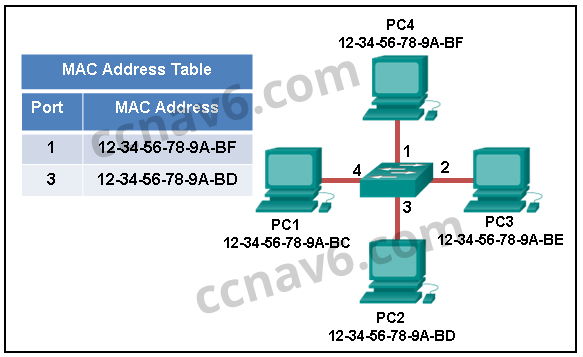




 Sort elements
Sort elements